Triangulation Fraud: A New Scheme That Lets Fraudsters Pose as Merchants
Fraud is a very big deal in the digital age. The ease with which consumers can search, shop, and purchase pretty much anything they want with a few taps on a smartphone or tablet provides a veritable breeding ground for scams of every stripe.
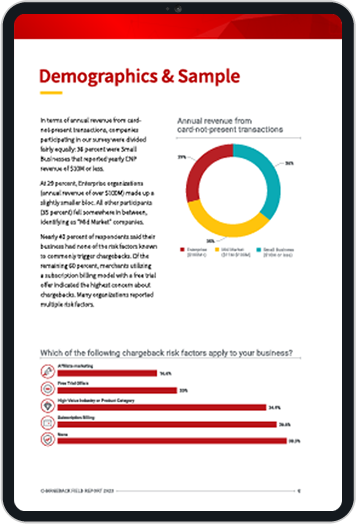
Triangulation fraud is one of the latest threats you need to be on the lookout for online. Let’s talk about it — we’ll examine what it is, how it works, and what you can do to insulate your business against attacks.
Recommended reading
- Address Fraud: How Criminals Swap Addresses to Abuse Victims
- How do Banks Conduct Credit Card Fraud Investigations?
- What is Wardrobing? How Can Retailers Stop Refund Abuse?
- Key Credit Card Fraud Statistics to Know for 2024
- Scammers See Opportunity as March Madness Begins
- Man-in-the-Middle Attacks: 10 Tips to Prevent These Scams
What is Triangulation Fraud?
- Triangulation Fraud
Triangulation fraud occurs when a customer makes a genuine purchase on a third-party marketplace, like eBay or Amazon, but the seller fraudulently purchases the product from another merchant. The name comes from the tri-lateral relationship between three involved parties: the unsuspecting customer, the legitimate merchant, and the fraudster middleman.
[noun]/* trī, ● aNGjyə ● lā ● SHən ● frôd/Triangle fraud involves three main players:
A scammer
A legitimate customer
A digital storefront
In essence, triangulation fraud happens when a fraudster hijacks the eCommerce buying process. They’re operating as a merchant and accepting orders. But, instead of maintaining their own store of merchandise, they’re using stolen cardholder data to purchase goods from a third party and then ship them to the buyer. Once the cardholder realizes they’ve been the victim of fraud, they file a chargeback to get their money back.
Does this sound confusing? Well, it’s meant to be. It’s a lot harder to track down the source of fraud if no one is really looking for it, and triangulation fraud scammers operate by using that fact to their advantage.
We conduct a lot of our business online nowadays, from paying bills to shopping and sharing private information. Unfortunately, attacks like these are bound to become more commonplace. The stakes, as they say, are high. That’s why it’s more important than ever to know what you’re up against, and have a plan to respond.
How Does Triangulation Fraud Work?
First, the fraudster sets up operations on a marketplace site. eBay is a popular option, but any site with a marketplace that allows third-party sellers to operate will work. The criminal then lists products for sale at unusually low prices.
When a cardholder makes a purchase, the fraudster then turns around and buys the goods from a legitimate seller using stolen cardholder information. The fraudster sets the shipping address to match that of the customer. The legitimate merchant then ships the product to the buyer.
The fraudster pockets the money from the original sale, while the legitimate merchant gets paid using a stolen payment card. This triangulation fraud loop can be repeated over and over again if the merchant lacks appropriate fraud detection tools and other safeguards in place to prevent abuse.
Of course, this becomes the merchant’s problem when the owner of the stolen information notices unauthorized charges on their statement. The cardholder disputes the charges, and the merchant ends up facing a wave of chargebacks as a result.
Triangulation Fraud is a Serious Threat
Many fraudsters have an attitude that suggests triangulation fraud is a victimless crime. After all, the consumers in question get the products they ordered, while the owner of the stolen credit card is not liable for fraud. As we pointed out above, though, merchants end up paying for the crime through chargebacks directed at their businesses.
Merchants caught up in triangulation fraud are often targeted over and over again. This forces consumers to exercise their chargeback rights to get their money back from the fraud they never instigated. In turn, the merchant is charged twice for every instance, which leads to a never-ending loop of lost revenue, rising prices, and legal headaches.
Current losses tied directly to triangulation fraud are unclear. However, triangulation fraud is a form of eCommerce fraud, and these CNP fraud attacks will collectively cost merchants around the world about $130 billion by the end of 2023. Given what’s at stake, triangulation fraud needs to be taken seriously, especially as these losses reverberate out, eventually impacting everyone in the payment ecosystem.Through escalating inflation, supply chain issues, and uncertain markets… absolutely everyone suffers because of fraud. While the average person might not immediately recognize rising prices and associate them with criminal activity, the broader trend is very apparent.
Common Sources of Data Used for Triangulation Fraud
As mentioned above, triangulation fraud isn’t easy to detect or identify. This is because the scammer is fulfilling genuine customers’ orders, using real shipping information, but with stolen credit card numbers that are usually bought in bulk on the dark web. Having that degree of separation makes the entire process feel random and hard to pinpoint.
How do hackers mine the credit card numbers they buy and sell for fraud? Here are a few of the methods scammers use:
It sounds grim, but don’t worry: there is good news, too. Triangulation fraud is actually pretty easy to eliminate once you identify it.
Identifying Triangulation Fraud
If you suspect fraudsters have targeted you for a triangulation scheme, the first step should be to review your analytics.
You want to look for those items which fraudsters seem to purchase repeatedly. Schemers involved in triangulation fraud are probably running a specialty operation, so they’re typically buying the same item (or items) over and over. Cosmetics, for instance, are a common target for triangulation fraud. If you identify problematic items, you can refine your fraud scoring rules and set a lower threshold for these goods.
You can also look at the payment method used. Are all the suspect transactions coming from a specific banking identification number (or BIN)? Are they all using the same payment method? If so, this can be a sign of fraudulent activity.
Another tactic you can employ if you suspect abuse is to put risky purchasers through additional checks. For example, you can charge two micropayments to the account in question and ask the buyer to verify the amounts.
Beyond those general fraud tips, there are some unique, recognizable signs of triangulation fraud to watch for as well. Below are a few common warning signs associated with a triangulation attack:
New Customers
A new account that suddenly starts buying the same items on a regular basis.
Conflicting Addresses
The buyer’s billing and shipping information are different.
Low Dollar-Value Transactions
Triangulation fraudsters typically focus on commonplace items not usually targeted by fraudsters.
Low Dollar-Value Transactions
Triangulation fraudsters typically focus on commonplace items not usually targeted by fraudsters.
Transaction Velocity
Triangulation attacks are usually committed by small groups operating repeatedly from a few devices.
You should watch for groups of transactions that display any of the warning signs outlined above. If you see these show up regularly, you may have a problem with triangulation fraud.
Looking beyond individual transactions, you may also want to try leveraging historical data to map out and link common and recurring points. This kind of comprehensive trend and link analysis can expose common attributes in a lot of triangulation fraud. Although time-consuming and labor-intensive, this is critical work: analyzing data in this manner lets you generate better data over time. That will make for more informed and intelligent decisioning.
How Do You Prevent Triangulation Fraud?
All the above-mentioned practices can help you detect and stop triangulation fraud. But obviously, the best approach to fraud is to prevent it before it happens.
You can’t afford to appear vulnerable. Fraudsters know that the more people who are engaged in fraud against a single merchant, the harder it becomes to detect bad orders and identify fraudsters. So, your fraud losses will grow quickly once a criminal ring identifies your site as a target.
It creates a feedback loop over time. Undetected fraud attacks generate bad data, making fraud detection less accurate, and the problem worsens over time. Overall, your best move is to stop fraud quickly and prevent it in the long term by adopting a multilayer strategy.
It’s true that adding more fraud tools to your screening process can be costly. However, you have to look at the overall cost to implement a solution and weigh it against the potential losses you could avoid. Think of fraud prevention tools like a net: the more tools you incorporate, the finer the mesh, and the finer the mesh, the more fraud you catch. And the more fraud you catch, the better your long-term performance.
A dynamic, comprehensive approach to fraud management should include:
- Address verification (AVS)
- CVV verification
- Geolocation
- Blacklists to ban known fraudsters
All the tools outlined above work side-by-side your fraud scoring processes to deliver better fraud decisioning. And, of course, first-party chargeback management tools like chargeback alerts and Intelligent Source Detection™ help eliminate genuine criminal fraud while also identifying cases of friendly fraud.
Triangulation fraud is just one of many threats that can separate you from your hard-earned cash. But, with an effective approach to chargeback management at your disposal, you have the power to prevent losses, recover revenue, and protect the long-term viability of your business.
FAQs
What is triangulation fraud?
Triangulation fraud occurs when a customer makes a genuine purchase on a third-party marketplace, like eBay or Amazon, but the seller fraudulently purchases the product from another merchant. The name comes from the tri-lateral relationship between three involved parties: the unsuspecting customer, the legitimate merchant, and the fraudster middleman.
How does triangulation fraud work?
First, the fraudster sets up operations on a marketplace site. eBay is a popular option, but any site with a marketplace that allows third-party sellers to operate will work. The criminal then lists products for sale at unusually low prices.
When a cardholder makes a purchase, the fraudster then turns around and buys the goods specified from a legitimate seller using stolen cardholder information and sets the shipping address to match that of the customer. The merchant then ships the product to the buyer but pockets the money from the sale.
Where does triangulation fraud come from?
Data breaches, mobile device hacks, phishing scams, and fraud as a service (FaaS) are all popular methods that scammers use to commit triangulation fraud attacks.
How can I tell if I’ve been a victim of triangulation fraud?
Triangle fraud does have some clear, recognizable signs to watch for. A few common warning signs associated with a triangulation attack include: conflicting addresses, low dollar-value transactions, invalid contact information, and a high transaction velocity.
As a merchant, you should watch for groups of transactions that display several of the warning signs outlined above. If you see these show up regularly, you may have a problem with triangulation fraud.
How do you prevent triangulation fraud?
It’s true that adding more fraud tools to your screening process can be costly. However, you have to look at the overall cost to implement a solution and weigh it against the potential losses you could avoid. Think of fraud prevention tools like a net: the more tools you incorporate, the finer the mesh, and the finer the mesh, the more fraud you catch. And the more fraud you catch, the better your long-term performance.
A dynamic, comprehensive approach to fraud management should include multiple complementary fraud tools, all backed by fraud scoring technology.