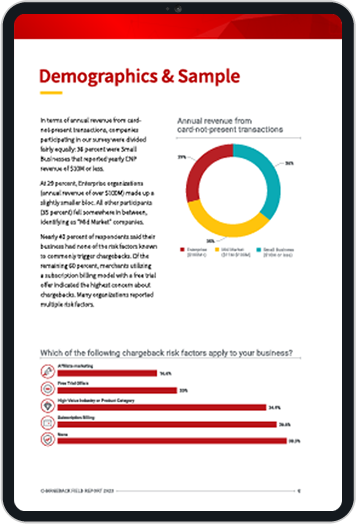
Payment SecurityAre You Doing All You Should to Protect Your Customers’ Data?
In a Nutshell
eCommerce connects buyers and sellers all over the globe… and electronic payment methods are what make eCommerce possible. Of course, what makes shopping easier for us also gives cybercrooks another opportunity to rip us off. In this post we look at ways to safeguard your payments processes and protect shoppers when they buy from you.
Payments Security: Tools, Tips, & Best Practices for Merchants
As a merchant, you’re in the business of selling. Right?
The trick is getting consumers to buy from you, and not a competitor. To do that, you have to offer something: better prices, wider selection, free shipping, or anything that makes your store more attractive.
Some of these offerings may be market-driven, but some are non-negotiable. At the top of that list is payment security.
Payment security consists of all the rules, tools, and protocols you use to protect the integrity of your business transactions. This includes securing transmissions, preventing fraud, and defending customers’ personal data against cybercriminals. The overall goal is to lock out the bad guys while still allowing customers to make legit purchases. Oh, and you want to accomplish this with as little friction as possible, so buyers won’t get frustrated and abandon ship.
Source: LexisNexis Risk Solutions
Admittedly, it’s a tall order: fraudsters seem to be developing new tricks and technology on a daily basis. Effective payment security is never going to be an off-the-shelf, “set it and forget it” endeavor. It takes a long-term, multifaceted approach that combines advanced tools, best practices, and ongoing vigilance. So let’s take a look at some of the things your plan should contain.
While we’ll primarily be talking about elements businesses should incorporate into their security plans, these are generally the same things a consumer should look for when paying a merchant.
Recommended reading
- How Online Payment Processing Differs From Offline Payments
- Payment Process Flow: Who’s Involved in the Process & How?
- Best Credit Card Processing Companies of 2025 REVEALED
- Credit Card Processing Fees: How to Lower Your Rate in 2025
- Payment Trends: Where Payment Processing is Going in 2025
- Alternative Payments: How to Take Payments Without Cards
Elements of Payment Security: Cybersecurity
To start with, there are security factors that should be built into your payments system already. If you’re missing any, now would be a good time to learn more about them.
Firewalls are just one way of protecting your business from the impacts of fraud. We know a few more.
Request a Demo
Elements of Payment Security: Customer Authentication
You want to set up things on your end to keep fraudsters out of your data. That said, a big part of digital payments security is authenticating your buyers, too.
But, how can you double-check customer IDs when you never actually meet face to face?
Customer verification demands the use of a variety of tools to confirm that the person on the other end of the order is actually who they say they are. There are several authentication methods you can deploy; you’re probably already aware of at least a few of these:
Elements of Payment Security: Fraud Detection & Monitoring
Having the perfect payment protection program in place today doesn’t mean you’re safe tomorrow. Staying one step ahead of cybercriminals is an ongoing endeavor which requires constant monitoring, analyzing, and adaptation to new threats.
Fraud Scoring
Fraud detection is critically important as a way of proactively mitigating the risk of financial losses. Advanced systems use artificial intelligence and machine learning, refining the ability to identify emerging fraud patterns and flag anomalies such as:
- Orders that vary from historical norms for that customer
- Unusually high ticket prices
- Multiple similar orders for the same customer
- Multiple identical orders for different customers
- Payments to blacklisted countries, or fraud-prevelant areas
Any of the above protocols offer some level of payment security online. Taking a multi-factor authentication (MFA) approach, however, adds an extra layer of security by necessitating two or more elements of verification from the customer, such as both a password and a fingerprint.
Data Analysis & Manual Auditing
Maintaining the most effective payment security means you need a way of keeping an eye on your payments system. Transactions need to be monitored in real time, so that any unusual behavior can be addressed quickly.
Consistent monitoring, though, also means a consistent flow of incoming information. Part of your payment security plan is analyzing this information and trying to spot anomalies, deviations, or patterns. Yes, you can (and should) have software that does the heavy lifting. But, it’s always a good idea for reports to be seen with human eyes.
A Final Thought
With the right tools, you can build a pretty solid security wall around your data and processes. That helps protect both your customer and your business from most types of fraud.
Unfortunately, prevention efforts aren’t going to work well with chargeback (friendly) fraud. Why? Because it happens days or even weeks after the transaction in question.
One thing to consider adding to your payment security plan is a comprehensive chargeback management strategy customized to your business. Contact us today to learn more.
FAQs
What does payment security mean?
Payment security refers to the specific tools, practices, and security measures merchants put in place to safeguard cardholder data that is stored, transmitted, or being processed.
What is the best payment security?
The best payment security comes from an integrated security system built around best practices like tokenization, data encryption, PCI DSS compliance, and consistent monitoring, among other factors.
Is payment security worth it?
Yes. A well-planned security strategy keeps confidential data — both yours and your customers’ — secure, preventing unauthorized access that could potentially lead to fraud/chargeback losses or even lawsuits.
What is the safest way to accept payments?
Despite the negative press they receive, credit cards are still considered one of the safest ways to pay. While there is no single payment method that is the safest under all circumstances, card payment security protects your buyers, plus offers comprehensive – and established – post-transaction fraud protection. ACH and virtual credit cards are also among the safest payment types.