Can EMV Bypass Cloning Let Fraudsters Copy Chip Credit Cards? If So, How Does it Work?
In a sense, it was bound to happen eventually.
When EMV chip cards hit the scene, they were pitched as being basically impossible to duplicate for fraud purposes. No technology is foolproof, though. Just when the world was getting comfortable with the security of credit card EMV chips, fraudsters pinpointed a way to bypass the technology.
So what does that mean for consumers and merchants? Are EMV cards still safe to use? Is this really as big of a problem as it seems?
Recommended reading
- What is Alipay? Can US Consumers & Merchants Use Alipay?
- How to Use a Contactless ATM & Where to Find Enabled Devices
- Terminal ID Number (TID): What is it? What Does it Do?
- Dispute Apple Pay Transaction: How Does The Process Work?
- Visa+: Get the Most Out of Digital Wallets With This Tool
- Mastercard Installments: How Mastercard BNPL Works
EMV Credit Cards: A Brief Overview
Before we dive in, it might help to get a little background on EMV technology.
For many years, a magnetic stripe was the standard way of storing personal data on a credit card. While payment cards still have that stripe, most credit and debit cards issued in the last decade now feature a square gold chip on the front, as well. That square is an EMV microchip. It’s a type of technology used to safeguard and transmit card information during transactions.
With magnetic stripe cards, cardholder data is permanently cached on the physical card. It can be read by anyone who has the proper equipment (merchants and fraudsters alike). This is not the case with EMV cards, though.
EMV (so called because it was developed by EuroPay, Mastercard, and Visa) cards create a unique encrypted code for each transaction. The data is tokenized, meaning that substitute, one-time-use data is transmitted in place of the valid card information. This makes purchases with chip cards much safer than magnetic stripe purchases.
Learn more about EMV technology
What is Chip Card Cloning?
Conventional wisdom says that EMV chips cannot be cloned. Technically that’s true; the chip itself cannot be cloned. The EMV card, however, is another story.
Like we mentioned above, EMV technology encrypts the card information stored on the chip, substituting a unique token for each transaction. That inherently makes the process more secure.
But remember: all EMV cards still feature a magnetic stripe, for situations where EMV chips can't be validated. The obvious solution for a fraudster is to somehow transfer chip information over to the card’s magnetic stripe. That’s exactly what researchers have managed to do.
As reported in Security Week, researchers recently demonstrated a new way to scam the system and bypass EMV verification. With the right tools, data can be extracted from an EMV chip. This data can then be used to create a magnetic stripe version of the same card. The perpetrator can use this card at any card-present merchant by simply claiming that the card issuer didn’t provide them with an EMV-enabled card.
Using both information sources on the card, fraudsters can turn a hack-proof chip into a fully functional payment card. This is what’s being referred to “EMV bypass cloning” or “chip card cloning.”
How Are EMV Security Features Bypassed?
Card cloning is dependent on the hacker having the card data ahead of time. With traditional mag stripe cards, this was accomplished by using a card skimmer. Attempting to steal EMV-protected data demands more sophisticated tools, though.
The preferred tool used for capturing the information necessary for EMV bypass cloning is a physical device called a shimmer. An example of a common shimmer device is seen in the image below:
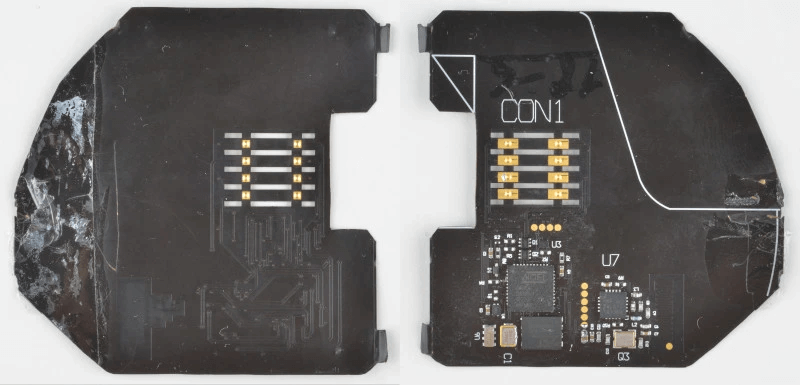
Credit: Hackaday
A shimmer is a chip-card cloning device that captures payment information mid-transaction. It can be attached to an ATM, gas pump, parking meter, or any other place at which people dip an EMV chip card.
The device is built on a cheap polyimide film-flexible printed circuit board. The shimmer is thin enough to be glued into the card reader, and is very difficult to detect.
Shimmers should not be confused with skimmers, which are another type of device commonly used for data theft. As the name implies, a skimming device “skims” data from the magnetic stripe when a card is swiped. In contrast, a shimmer reads the data from an EMV chip, just like a legitimate card reader would do.
Once they have that information, it’s relatively easy for fraudsters to clone the victim’s card with a card that has a non-functioning EMV chip, but a fully enabled magstripe. They can then use the bogus card to commit payment fraud the same way they would with any non-chip card.
Is EMV Bypass Cloning New?
Yes and no. The knowledge that magnetic stripe cards could be made from EMV chips isn’t new. The notion that cloned EMV cards were theoretically possible was reported back in 2008. What’s new are the tactics that fraudsters use.
Although chip card cloning was possible, nobody really worried about it at the time. Banks and card networks knew that the ultimate goal was to phase out magnetic stripes altogether. Without both components, EMV cards could not be cloned.

But, obviously, magnetic stripes have not been eliminated yet, and probably won’t be for several years, at least. That’s why an extra security code was introduced into EMV chips.
To further ensure the safety of card data, EMV chips have an additional security component that the stripe does not have. Banks are mandated to check for this code before approving any transaction, from now until magnetic stripes disappear for good.
It was a simple enough solution, and to be fair, most banks adhere to this rule. Some failed to follow this requirement as closely as they should have, though. Apparently, they assumed the data would still be safe. After all, the “EMV-to-magstripe” possibility was still only a theory… right up until it wasn’t.
How Big of a Problem Is EMV Bypass Cloning?
It’s big.
The practical viability of this EMV chip card cloning technique was proven when researchers from Cyber R&D Lab conducted an experiment using cards issued from 10 different banks. They were able to capture personal data from four of those cards, from which they created cloned magstripe cards and made purchases.
So, not only is card cloning possible, studies suggest that the method is already being used by the cybercriminal underground. And, in another recent report, security firm Gemini Advisory announced it had discovered two instances of hackers offering harvested EMV card data for sale on the dark web.
More formal proof that criminals are now targeting EMV card data came from an alert sent out by Visa. The card network warned that POS malware strains like Alina POS, Dexter POS, and TinyLoader had been updated to collect EMV card data, indicating that the card brand knows that the data could be monetized.
But, while the problem is no longer theoretical, there are still not many indications that the technique is in widespread use (at least not yet). That could change quite quickly, of course, if major cybercrime rings jump onto the bandwagon. The effect could undermine the safety of EMV protection, erode consumers’ faith in credit cards, and expose merchants to increased chargeback risks.
Can Card-Cloning Fraud Attacks Be Prevented?
For all the potential dangers of EMV bypass cloning, the best solution is both easy and obvious: banks need to consistently take advantage of EMV’s built-in security features.
All of the reported attacks would have failed if a simple data integrity check had been performed at the time of purchase. Relentlessly verifying security codes on all transactions would effectively eradicate the problem across the board.
This responsibility can be shared by merchants, who should make a point of regularly inspecting physical terminals for the presence of illegitimate hardware. Online merchants should insist on validating card CVVs on all card-not-present purchases, as even a cloned EMV card will still not produce a CVV match.
Finally, consumers need to up their fraud-prevention game, as well.
For example, when using an ATM — particularly one not associated with their bank — cardholders should check for any obvious signs of tampering on the device. They should check the top of the machine, as well as near the side of the screen, and on the card reader and keyboard. If something looks fishy, such as slight color or material difference, graphics that don’t line up, or anything else that doesn't look right, that ATM should not be used.
The same rule applies for any publicly-accessible card reader, like a gas pump or other unattended terminal. If something seems off… play it safe.
EMV Chips: Still Safe, but not a Silver Bullet for Fraud
EMV chips were a breakthrough for payment card security. While EMV bypass cloning has been shown to be possible, a little extra diligence can nip the problem in the bud.
That said, EM chip cards simply aren’t designed to prevent every kind of fraud. Think about post-transaction attacks, such as invalid customer disputes, for example.
For merchants, effective fraud and chargeback management requires more than just a couple of quick tweaks to stay current.
Businesses need to combine traditional fraud prevention techniques with a comprehensive chargeback management plan to maximize their efforts. If you’re ready to take your chargeback defense to the next level, we can help. For more information, contact Chargebacks911 today.
FAQs
Are EMV cards secure?
In general, yes. Chip cards are safer and more secure than traditional credit cards that only have magnetic stripes, because all personal information is encrypted and tokenized for each transaction. However, there are devices that can enable scammers to steal EMV chip information.
Can an EMV card be cloned?
Yes and no. EMV chips themselves cannot be cloned. However, fraudsters can create a workable card clone by copying data from the card’s chip and transferring it to a magnetic stripe card.
How do fraudsters clone cards?
Fraudsters use skimming devices acting as card readers to collect the victim’s credit card information via the magnetic stripe on the back of the payment card. EM cards are different, though; to obtain data for EMV cloning, crooks use a different device called a shimmer.
Do you get your money back if your card is cloned?
Yes. Transactions made using a cloned card are considered unauthorized. Therefore, consumers can usually get all their money back for any fraudulent use by filing a chargeback.
Can you go to jail for cloning cards?
Absolutely. Depending on the situation, thieves may face up to 15 years in prison and up to $25,000 in fines at the state level. If the case falls under federal jurisdiction (for instance, if the fraud crosses state lines), the penalties can be even greater.