How to Spot and Stop Clone Phishing Attacks: 20 Tips for Consumers & Merchants
Imagine getting an email from one of your favorite brands. But, the content feels slightly… off, somehow.
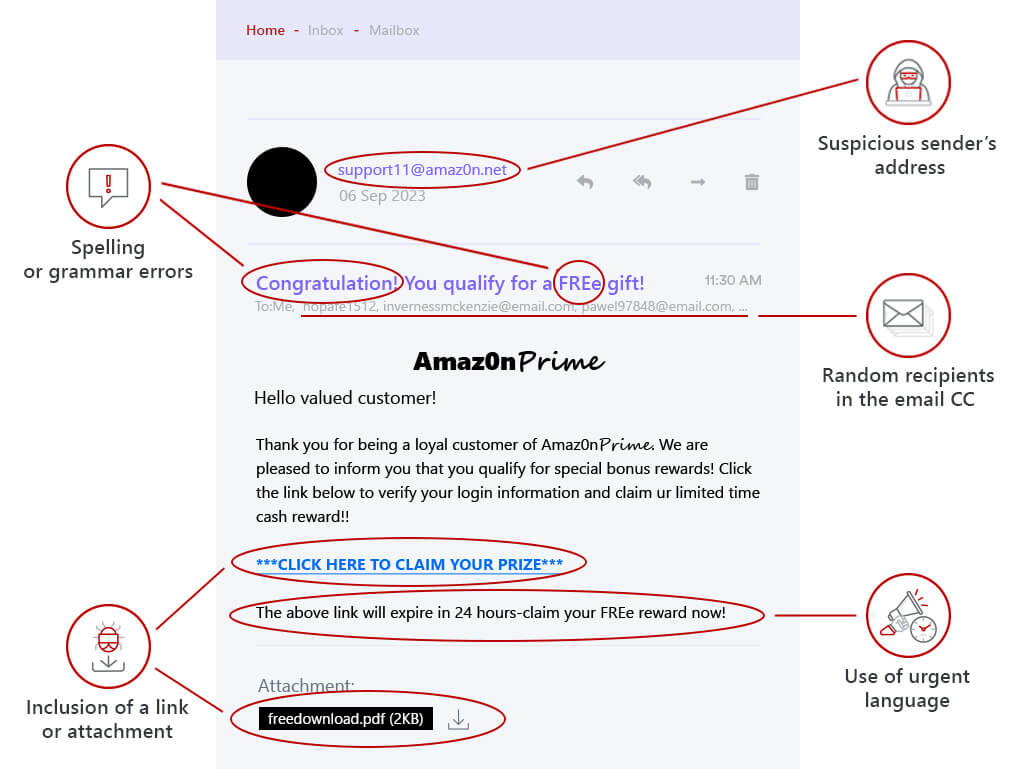
You spot several typos in the email. There’s also a pushy call to action, prompting you to click on a soon-to-expire link. Digging deeper, you realize the sender's address is not the one you're familiar with. You hover your cursor over the link, and see that it directs you to an unsecured site, rather than the retailer’s homepage.
Could this be a scam? Probably. In 2022 alone, there were over 500 million attempted phishing attacks. Many of them began with suspicious emails just like this one.
This tactic, by which fraudsters impersonate trusted brands to deceive and extract information, is called clone phishing. Impersonators send out scam emails harboring malicious links and files, with the goal of compromising your online security.
Recommended reading
- What is Mastercard SecureCode? Here’s How it Works
- The Top 10 Fraud Detection Tools You Need to Have in 2025
- ECI Indicators: How to Understand 3DS Response Codes
- How to Detect Fraud: Top 20 Tips to Stop eCommerce Scams
- Reverse Email Lookup: Tips, Tools & How to Detect Fraud
- Top 20 Fraud Red Flags All Merchants Should Know in 2025
What is Clone Phishing?
- Clone Phishing
Clone phishing is a phishing tactic by which a scammer impersonates a well-known brand, then sends emails or other messages on that brand’s behalf. The goal is to trick victims into clicking a link that will infect their device with malware or compromise their identity in some other way.
[noun]/klōn • fiSH • iNG/With clone phishing, cybercriminals mimic genuine emails with the intent of distributing malware. These fraudsters often capture a legitimate message from a trust party, like a bank or major retailer. They then alter it and redirect it to potential victims.
Copying and altering an email style used by a legitimate brand will make their modified email look more legitimate. However, it features a hazardous attachment or link, replacing what was once a trustworthy call to action.
People are often fooled by clone phishing emails because they look so much like the real deal. A clone email might seem like a message from your bank, a customer service notification, or even a regular update from a company you trust.
Once you click that link, however, these fraudsters can dive into your personal information. They can gain access to your payment information or other personal data. They can use these to launch additional attacks.
How is Clone Phishing Different From Other Phishing Scemes?
Phishing has become an increasingly common cybercrime. As we mentioned above, there were over 500 million reported attacks in 2022 alone; more than double the number of incidents reported in 2021.
It's easy to see why so many fall for phishing attacks. That said, different phishing scams target users in different ways. Spear phishing, for instance, is a highly targeted tactic, with scammers using detailed information to target specific individuals. Other tactics like whaling, smishing, and vishing exist as well.
Learn more about phishingClone phishing is unique in one key area. Most phishing attempts create a fake message to target users with a specific call to action. In contrast, clone phishers take genuine emails, then alter them to substitute safe elements like links and attachments for harmful content and fake domains.
How Does Clone Phishing Work? 3 Common Examples
Some clone phishing attempts are amateurish and fairly easy to spot. However, skilled scammers can excel at mimicking a brand's communication style, making it seem like they are authentic representatives.
These fraudsters are pretty clever, often basing their tactics on reputable brands' notifications during security incidents or vital updates. With that in mind, here are a few common clone phishing tactics you should be aware of:
The above are just a few examples of clone phishing in action. Next, let’s dig into some tactics you can use to spot one before it’s too late.
How to Spot Clone Phishing
Be wary of any email that feels a bit off, or which seems to rush you into acting quickly. It might be a clone phishing attempt.
Sadly, many folks only catch on to the scam after they've unintentionally downloaded malware or given away their login details. Below is a handy guide outlining typical clone phishing red flags, that may help you detect a scammer:
| Red Flag | Indicator |
| Inconsistent Links | When the hyperlink's text doesn't match the website it directs you to. |
| Suspicious Domain | The sender's email domain doesn't match the genuine domain of the organization they say they represent. |
| Pressure Tactics | Messages pushing you to act immediately, or which make you feel like there's no time to think carefully and double-check details. |
| Email Alerts | Alerts or warnings from your email client or antivirus tools flagging the message as suspicious. |
Remember, while these signs can be helpful, they aren't guaranteed detection methods by themselves. Not all clone phishing attempts will come with obvious pressure tactics. That said, we've put together some strategies below that should help consumers stay safe, as well as another list of tips targeted at businesses.
Remember: when it comes to online fraud, no one is safe.
10 Tips to Prevent Clone Phishing: Consumers
As we mentioned above, clone phishing attacks can be difficult to detect. However, that doesn’t make them foolproof. There are several cybersecurity tips that can help protect your personal information from scammers:
#1 | Embrace Password Managers
These tools act as your first defense against deceptive websites. Be wary if you’re on a familiar site, but it doesn’t autofill your credentials as it usually would.
#2 | Regularly Monitor Your Inbox
One of the best shields against phishing is recognizing how businesses reach out. The more familiar you are, the easier it is to spot an imposter.
#3 | Preview Links First
Hover over links in most browsers to see a sneak peek of the destination. If it seems off, it might be designed to direct you to a different location than what was suggested.
#4 | Keep an Eye Out for “HTTPS”
This prefix is like a digital safety seal. If it's missing, tread carefully; this means the site is not operating on a secured, encrypted web protocol.
#5 | Scrutinize Website URLs
Stumbled on a shady link? Inspect the website's address. Beware if it looks like something familiar but has subtle differences like typos or numbers in place of letters.
#6 | Maintain Your Cool
Clone phishers often try to tap into your panic response by urging swift action. Breathe. Review urgent-sounding messages with a discerning eye.
#7 | Examine the Sender's Details
Deceptive email addresses can eerily mirror genuine ones. A closer look might reveal subtle deviations that hint at a scam.
#8 | Be on the Lookout for Spoofs
Some phishing ploys mimic ongoing email threads. If an email “reply” lacks a genuine conversation starter, it may be a scam.
#9 | Validate with Reliable Sources
Got an odd email from a known brand? Reach out via their official channels to authenticate its legitimacy.
#10 | Report Suspicious Emails
Should you suspect a phishing attempt, you should respond by resetting all your passwords and notifying relevant parties promptly.
10 Tips to Prevent Clone Phishing: Businesses
Merchants should treat defense against clone phishing as one part of a comprehensive fraud prevention strategy. Since phishing attacks are often used to target employees, fostering an environment of continuous learning and vigilance is an essential first step. Consider these proactive measures:
#1 | Train Your Staff
Give regular briefings and training on the intricacies of phishing, facilitated by seasoned experts, either from within your organization or external consultants.
#2 | Embrace Email Encryption
When transmitting highly confidential data, encryption is your digital seal of trust. All sensitive data must be encrypted before being transmitted.
#3 | Vet All Attachments
Every attachment should face the scrutiny of robust antivirus software to weed out hidden malware or suspicious code.
#4 | Collaborate on Link Verification
Encourage a culture of cross-checking. Sharing and verifying links amongst colleagues can act as a secondary safeguard against deceptive destinations.
#5 | Stay Alert to SSL Certificate Red Flags
Cyber impostors often skip the nuances, like securing genuine SSL certificates and banking on users' oversight. Train your team to spot these discrepancies.
#6 | Exercise Caution With Browser Plugins
Some clone phishing attempts can impersonate legitimate browser plugins, waiting to snatch data upon login. Keep an eye out for suspicious plugins.
#7 | Decode Generic Errors
A bland, nondescript error message, instead of a website's typical customized alert, might be a case of a “wolf in sheep's clothing.”
#8 | Navigate Pop-Ups Wisely
Intrusive pop-ups might be more than mere annoyances; they could be phishing lures. Always verify a site's legitimacy via the address bar before engaging.
#9 | Perform Regular Backups
Ensure that all data is backed up regularly. In case of a security breach, having an updated backup can prevent loss of crucial information and allow for fast recovery.
#10 | Foster a Reporting Culture
Encourage employees and clients to report suspicious emails or activities. This helps address potential threats promptly and creates an environment of security vigilance.
New Threats Develop Every Day
Clone phishing is the stealthy cousin of conventional phishing. Scammers are constantly refining their tactics, though, looking for new ways to lure and deceive victims.
Staying informed about the latest phishing nuances ensures you're always ahead of digital scams. That said, don’t forget that there is no such thing as a “one-size-fits-all” solution to fraud.
To truly get the most out of your fraud prevention investments, you need to formulate a multilayered strategy. Your defenses need to be capable of addressing threats from every angle, including illegitimate chargebacks. Click below to learn more.
FAQs
What is a cloning attack?
Clone phishing involves cybercriminals mimicking genuine emails with the intent of distributing malware. These fraudsters capture and alter a legitimate message before redirecting it to potential victims. The modified email replaces a trustworthy attachment or link with a hazardous one.
What does cloning mean in cyber security?
In cybersecurity, “cloning” refers to the act of creating an exact replica of a legitimate website, email, or system to deceive users. Fraudsters use this tactic to steal sensitive information or spread malware. Being aware of cloning helps users identify and avoid potential threats.
What is an example of clone phishing?
Clone phishing occurs when cybercriminals replicate a legitimate email, making subtle changes to deceive the recipient. In this scam, a seemingly familiar message might contain a malicious link or attachment. Unsuspecting users, believing the email is genuine, might click the link or open the attachment, leading to data theft or malware infection.
What is clone phishing used for?
Clone phishing is used by cybercriminals to replicate legitimate emails with deceptive changes, aiming to trick recipients into clicking malicious links or opening harmful attachments. This tactic seeks to steal sensitive information or introduce malware. It capitalizes on trust by mimicking known sources.
What is the difference between clone phishing and spear phishing?
Clone phishing involves replicating a legitimate email with slight alterations to trick the recipient, typically targeting a broad audience. Spear phishing, on the other hand, is a targeted approach where the attacker customizes the deceptive message for a specific individual or organization, often using gathered information to increase the email's credibility. Both aim to deceive, but spear phishing is more personalized.















