8 Ways You Could Be Targeted By Business Email Compromise Scams & How to Respond
Concerned about people in your organization getting tricked by a business email compromise (or BEC) scheme? Or, maybe you’ve already been hit by a BEC scam, and you’re hoping to recover and to prevent it from happening again.
Whatever the case may be, business email compromise is of serious concern for businesses in just about every vertical. It doesn’t matter if it’s retail, medicine, travel, or finance: businesses are losing billions of dollars to these clever attacks, and the problem is getting worse every year.
What exactly does BEC entail, though? How does it work against you, and most importantly, how do you fight back? Let’s find out.
Recommended reading
- Package Redirection Scams: Tips to Stop Them From Happening
- The Top 10 Prepaid Card Scams to Watch Out For in 2024
- How do Banks Conduct Credit Card Fraud Investigations?
- What is SIM Swapping Fraud & How Does It Work?
- Key Credit Card Fraud Statistics to Know for 2024
- Scammers See Opportunity as March Madness Begins
What is a Business Email Compromise Scam?
- Business Email Compromise
Business email compromise, commonly abbreviated to BEC, is a scam conducted through email. With a BEC attack, an email will appear to come from a legitimate source within the business. However, the sender is an imposter attempting to trick other members of the organization to divulge sensitive information.
[noun]/biz • nəs • ē • māl • käm • prə • mīz/Business email compromise is not a conventional form of transaction fraud. Nonetheless, it's one of the costliest business scams active today.
Attackers that use BEC tactics exploit the fact that professionals and companies rely heavily on email for interpersonal communication to conduct business. In many cases, the scammer makes a request that could seem reasonable at first glance. The target sees the name on the email and, without thinking twice, provides the information requested.
Attackers may even use BEC to target the customers or clients of a business, making the problem even greater. To illustrate, here are a few examples of how this can play out:
- A company executive asks an assistant to buy a bundle of gift cards for employee rewards. Once the purchase has been made, they will request the serial numbers in order to email them out immediately.
- A homebuyer receives an email from the title company instructing them to wire a payment, either to cover a last-minute fee or as a preliminary share of the down payment.
- A trusted company vendor emails an invoice with an updated mailing address or payment details.
These aren’t random hypothetical situations. Each of the above are real-life cases that have actually happened to multiple people.
As you can plainly see, BEC scams are hard to identify. And, while directors and people in the C-Suite are common targets, scammers may potentially attack anyone within your company. A simple email could lead to losses in the thousands or even millions of dollars.
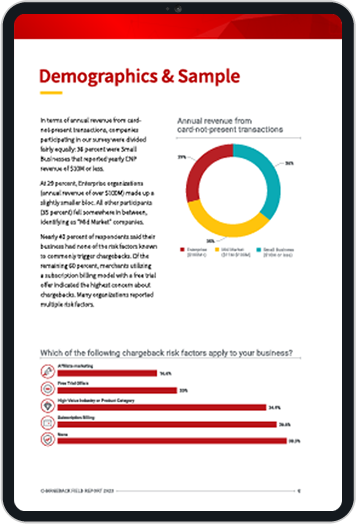
BEC Scams: A Massive Problem for ALL Businesses
Business email compromises can cost as much as $5 million per breach. Indeed, the issue is so incredibly serious that the FBI has labeled BEC the “the $26 billion dollar scam.”
If those numbers seem surreal, keep in mind, the threat is only growing. In 2020 alone, fraudsters scored nearly $2 billion dollars through BEC attacks. That’s considerably more in terms of raw dollar value than any other type of cybercrime.
Still having trouble grasping the gravity and scope of this threat? Here are five recent BEC scam and their estimated losses to convince you that no business is immune:
These are just a small fraction of the total BEC fraud that has swept the globe in the last decade. But, now that we know and understand the scale of the threat, we still have to determine how these attacks really work. And more importantly, how can you tell when a business email scam is in progress?
How Do BEC Scams Work?
Unlike many other scams, business email compromise attacks don’t require specific technological know-how or savvy to execute. Instead, any determined fraudster with the motivation and time to do their homework on your business can try their hand like this.
Remember, a scammer only needs to know the emails of the individuals involved and their roles within the company to attempt a BEC attack. This is information that can be gleaned from a simple LinkedIn search. Therefore, BEC scams are able to reap maximum rewards with comparatively little effort.
BEC attacks typically follow this pattern:
That last point is why rapid response times are utterly crucial for cybersecurity incidents.
Businesses that are slow to respond often never recover their lost funds and have very little luck locating the fraudster. Fast response could mean the difference between recovering funds and losing millions.

8 Common BEC Scam Techniques to Watch for
Business email compromise attacks rely on social engineering to select and groom victims. This is often easily accomplished without much technological expertise or tools, which generally helps to make business email compromise scams widely popular among fraudsters.
What specific practices do scammers engage in to conduct BEC attacks, though? Below, we’ve outlined the eight most common business email compromise tactics:
Tactic 1 | Exploiting Relationships
The easiest way to launch a BEC scam is to take advantage of an established professional relationship or network. This exploitation could look like a trusted vendor requesting payment of an invoice, employees sharing payroll direct deposit information, or an executive requesting the purchase of gift cards.
Tactic 2 | Fake Workflows
Presume your business uses an internal workflow management system to organize tasks. Many of these workflows will be assigned and communicated through a company email server, and can become second-nature to individual employees.
Some BEC attacks will attempt to replicate these workflows in the hope that an employee will act before much thought is given to the process. Examples of fake workflows might include internal emails requesting a password reset, emails from related or commonly used applications asking for access, or emails regarding shared documents for which you need to grant access.
Tactic 3 | Socially Engineered Content
In order for a BEC scam to work, the sender of the email must appear trustworthy. There must also seem to be a sense of urgency or familiarity involved to encourage the victim to action. Subject lines are key here and commonly include the following terminology:
- “Hello, [FIRST NAME]”
- “Immediate Action”
- “Payment”
- “Overdue”
- “Request”
Keep in mind that BEC attacks differ from phishing emails because they use language rather than external links to promote the scam. To that end, the emails sent will feature language that a victim will either click by rote or because they elicit a sense of official urgency.
Tactic 4 | Suspicious Attachments
Your company’s security mechanisms will be adept at defeating conventional malware attacks or suspicious links that come from unknown sources. However, BEC relies on social engineering in the form of internal communication or invoicing that would otherwise seem legitimate.
Any documents, spreadsheets, or data sent in the email are all designed to convince the victim that the email is coming from the source it is emulating.
Tactic 5 | Using Free Software
Fraudsters may use downloadable software that helps them to sneak past your company’s security mechanisms. Scammers can use software like SendGrid to create spoof emails and domains that can fool Google mail and other servers. By that same token, fraudsters can use Google Docs to extract sensitive data, send phishing links, or produce fake invoices in Google Box and Google Drive.
Tactic 6 | Executive Fraud
BEC scammers will impersonate a company’s CEO or other executives in order to target their employees. The request is usually made to an accounting or financing department employee and is intended to encourage the transfer of funds to the fraudster’s chosen account.
Tactic 7 | False Legal Representation
This BEC technique has the fraudster posing as a lawyer or other legal representative, usually over the phone or via email, who will then ask for an executive or employee’s personal information. This attack generally targets lower-level employees and new hires that might not think to question such a request.
Tactic 8 | False Vendor Invoice
If your company uses a lot of overseas or long-distance vendors, a savvy scammer could pose as that supplier to request payment of fake invoices, or report billing issues that lead to the payment of non-existent bills. Again, they might try to target junior employees who would not necessarily be familiar with all the vendors with whom you contract.
Which Fraud Tactics Do Legacy Email Security Technologies Prevent?
| Delivery | Techniques | Legacy Email Controls | |
| Spam | Mass email | N/A | |
| Mass phishing | Mass email | Mass-produced phishing kits | |
| VIP impersonation | Gmail/Yahoo, lookalike domains | Social engineering | |
| Payoll fraud | Gmail/Yahoo, lookalike domains | Impersonation, social engineering | |
| Vendor fraud | Email from compromised account | Impersonation, social engineering | |
| Credential phishing | Email from compromised account, Gmail/Yahoo | Redirects, brand impersonation for login pages, 0-day domains | |
| Account takeover | Credential phishing attack | Auto-forwarding rules, lateral movement |
It might seem obvious that employees should be cautious of links and emails that ask for money. However, the scam is so often successful because it exploits a power dynamic. After all, how many employees go around questioning direct orders or requests from their boss?
That said, it isn’t just a matter of screening emails to prevent BEC fraud. Let’s talk about your options here.
Preventing Business Compromise Attacks
As mentioned in our opening sections, business compromise attacks aren’t going away. These scams are far too lucrative to simply fade into the woodwork. This can only mean that businesses and their employees must be vigilant and prepared to face the issue head-on.
How do you do this effectively without a drop in revenue or productivity, though?
A multi-tiered fraud prevention strategy is extremely effective against fraud. Before we get to that point, though, a few best practices might make all the difference between an unwitting victim and a wise employee. We recommend that you train employees to:
Pro Tip: Your employees should not have access to monetary accounts without effective safeguards in place. For example, if a CEO suddenly emails an accounts payable employee to ask that funds be transferred under any circumstances, it might be wise to ensure that the email is approved by the CEO or through various personnel before funds can be transferred.
Diversify Your Fraud Prevention
Fraud isn’t a static problem encompassing. To best protect your business from one form of fraud, it’s a good idea to work to prevent as many types as possible by deploying fraud detection tools that work together to stop fraud before it starts.
Merchants need to stay a step ahead of fraud to be effective at protecting their businesses. They have to always anticipate where criminals might strike next. The good news: they don’t have to do it alone.
That's where Chargebacks911® comes in.
No matter where you need help, Chargebacks911 should be an integral part of any multilayer fraud management solution. We can work with your in-house management team to create a customized integration, offering the most comprehensive, transparent, end-to-end outsourcing options available. Plus, aloof our services are backed by the industry’s only performance-based ROI guarantee.
Don’t lose another to fraud and chargebacks. Contact us today to learn more about our solutions and how Chargebacks911 can help optimize your current fraud management efforts.
FAQs
What is business email compromise (BEC)?
Business email compromise, commonly abbreviated to BEC, is a scam conducted through email, usually on an interpersonal level within a business. With a BEC attack, an email will appear to come from a legitimate source within the business. However, the sender is an imposter attempting to trick other members of the organization to divulge sensitive information.
Why is business email compromise such a big problem?
Business email compromises can cost as much as $5 million per breach. Indeed, the issue is so incredibly serious that the FBI has labeled BEC “the $26 billion dollar scam.” If those numbers seem surreal, keep in mind, the threat is only growing. In 2020 alone, BEC fraudsters scored nearly $2 billion dollars this way… a number considerably higher than losses associated with any other type of cybercrime.
How does a business email compromise attack work?
Essentially, BEC scams are conducted through email, usually on an interpersonal level within a business. The fraudulent email will appear to come from a legitimate source within the business and is usually making a seemingly legitimate request.
What is an example of a business email compromise?
In the commonly-used executive fraud scam, for instance, BEC scammers will impersonate a company’s CEO or another executive in order to target employees. The request is usually made to an accounting or financing department employee and is intended to encourage the transfer of funds to the fraudster’s chosen account.
What's the difference between phishing and business email compromise?
Among other things, BEC scams differ from most schemes because they have specific targets in mind. They look more legitimate, and often appear reasonable or well within the parameters of normal business operations. In this way, cultivated deception is key.