Credit Card Shimmers: How This Simple, Cheap Technology is Helping Criminals Defeat EMV Cards
When EMV technology was rolled out in the US in 2015, it was pitched as a means to bring an end to card-present fraud. The technology made conventional card “skimming” impossible, and also made it much harder for fraudsters to create counterfeit credit cards.
Fraudsters are resourceful, though. In the years since the EMV liability shift, they’ve figured out a workaround for EMV chip protections. Everyone — consumers and merchants alike — is at risk.
With the rise of so-called credit card “shimming,” payment card skimming attacks have spiked 700% in 2022. So, what is card shimming, and how can you protect yourself?
Recommended reading
- Fake Google Reviews: How to Identify, Remove & Prevent
- The Top 10 Prepaid Card Scams to Watch Out For in 2025
- How do Banks Conduct Credit Card Fraud Investigations?
- How Card Cracking Works: Tactics, Red Flags & Prevention
- Credit Card Cloning: How it Works & How You Can Prevent It
- How Overpayment Scams Work: Signals, Examples & Prevention
What is a Credit Card Shimmer?
- Credit Card Shimmer
A credit card shimmer is a device designed to illegally capture data stored in the microchips implanted in EMV-compliant debit and credit cards. Shimmers are very tiny, thin devices that can be fitted into a card terminal, and can read EMV microchip data much in the same way that skimmers can read magstripe data.
[noun]/kre • dət • kärd • SHi • mər/Shimming devices were developed as a means to work around EMV microchips, which have all but replaced magstripe stripes that skimmers used to rely on. The tech is so insidious it would be fair to describe card shimming as “skimming 2.0”.
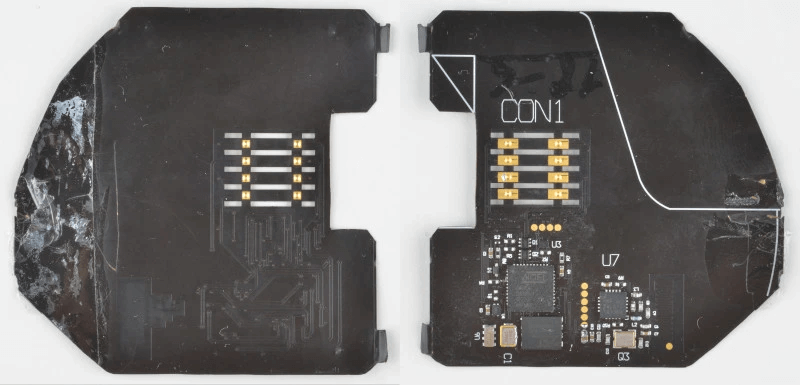
Credit: Hackaday
Fraudsters can't yet fully "clone" an EMV chip that's encoded with a valid user's information. However, they can copy the information stored on an EMV chip using a shimmer, then encode that onto a magnetic stripe card.
The fraudster can use the dummy card at any card-present retailer which allows customers to use a magnetic stripe card. Since mag-stripe cards are still commonly accepted when EMV chips are not available, this means a fraudster can effectively clone your chip card.
Card Shimmers vs. Card Skimmers
So, what’s really the difference between card skimming devices and newer “shimming” devices?
Where the two differ is in the target. Skimmers rely on the static information stored in magnetic stripe cards to steal card credentials. This data can then be copied and uploaded to a counterfeit magstripe card. If you don’t swipe, they can’t copy or clone this data.
Skimmers and shimmers are both tiny, often paper-thin devices that fit inside the card terminal directly between the card and the reader. The device itself is so small and innocuous that it’s extremely easy for fraudsters to slip them inside the card slot and very difficult for users to detect. They can also be loaded onto the front of a terminal or ATM machine.
Skimmers read information off of the magstripe included on the card. Shimmers, on the other hand, capture data located inside the EMV microchip that is embedded into your card. The data collected will then be offloaded wirelessly via a small radio module built into the device.
Thankfully, shimmers aren’t exactly infallible. For instance, the data stolen can’t be immediately used by the fraudster. If a PIN reader isn’t present, it must be uploaded and then cloned to a separate magstripe card.
Shimmers are also still quite rare… at least for now. As EMV chips increasingly become the standard, though, shimming is bound to take off and grow rapidly. We’re already seeing the beginning of that trend now.
How Big of a Problem is Card Shimming?
Big. Consider the 700% leap in skimming activity mentioned above. Much of that is related to card shimming scams.
EMV was meant to be the “silver bullet” for card-present fraud. Now, though, we’re seeing more sophisticated card shimmers capable of capturing dynamic transaction keys embedded into EMV chips. That means we’re in serious trouble.
The technology is still very new. There’s not much in the way of adequate data yet to accurately diagnose the scale of the risk associated with shimmers. However, we can say that this is a developing story that will determine future shopping and verification trends.
If EMV data is no longer safe, the impacts will reverberate through every industry linked with payments. With all the time and resources poured into EMV mandates, we could be back at square one for in-person fraud. Not only that, but we must also contend with the surge in card-not-present fraud resulting from the initial EMV liability shift. Online scammers won’t leave online channels and go back to brick-and-mortar; they’ll just take advantage of the opportunity to commit more fraud.
Why are Criminals Switching to Card Shimmers?
Shimmers have actually been around for a few years now, but they only started gaining in popularity fairly recently.
EMV cards use CVV3 verification technology, which is much harder to crack than the older versions of CVV technology used by magstripe cards. Trying to work around CVV3 technology requires a lot more effort than a simple scan and copy. CVV3, unlike CVV1 and CVV2, does not contain static data, meaning that it changes with each transaction.
The theory is that CVV3-enabled chip cards can prevent the majority of in-person fraud. This may be true to some degree, but it also poses another problem. Without the ability to easily copy and counterfeit cards, fraudsters have been forced to do the same thing as banks and financial institutions the world over: innovate.
Shimming essentially allows fraudsters the means to circumvent EMV standards without tipping off CVV3 verification methods. In short, the fraudster can avoid these safeguards altogether and take that information wherever a magstripe swipe is still available.
How Cardholders Can Prevent Card Shimming
Cardholders do have some recourse if they fall victim to fraud. They may be able to file a chargeback and recover their funds. However, this may be a long, protracted process, and there’s no guarantee that it will succeed. That’s why it’s best to prevent fraud from happening whenever possible.
It’s important for cardholders to opt for the newest security features whenever available. They can look for gas stations, grocery stores, and shops that allow for the use of NFC (near-field communications) technology to complete transactions. They can also try using mobile wallet apps like Apple Pay or Google Pay, which will facilitate contactless payments.
Currently, shimmers have no real impact on contactless transactions. So, cardholders should take advantage of this payment option wherever available.
Cardholders should also try to refrain from withdrawing funds from ATMs located in unsecured locations, like unattended, outdoor ATM machines. It is much safer and more secure to transfer funds with your mobile wallet or opt for P2P (person-to-person) payment applications like Zelle or Cash App.
Frankly, the best we can do at the moment is to increase awareness of the issue as much as possible and respond accordingly. And, as always, never count on just one method of fraud prevention.
What Can Merchants Do?
Merchants typically get the short end of the stick when it comes to fraud, even when there’s no obvious way for them to avoid being targeted. That said, merchants can drastically reduce the risk of shimming scams through a combination of effective fraud tools and best practices.
Here are a few tips for merchants to prevent credit card shimming:
Multi-Layered Strategies Work Best
Fraud prevention isn’t a one-way street. What works for one business may not necessarily work for another.
Also, not every fraudster is apt to try the same tactic twice. Merchants need to be nimble, adaptable, and willing to embrace multifaceted fraud management strategies.
Thankfully, this isn’t something you have to suffer through alone. With over a decade in fraud prevention and chargeback management, Chargebacks911 is uniquely placed to help consumers and merchants adjust to an ever-changing fraud landscape. Call us today for your free ROI analysis.
FAQs
What is a card shimmer vs. skimmer?
Skimmers and shimmers are both tiny, often paper-thin devices that fit inside the card terminal directly between the card and the reader. Where the two differ is in the target. Skimmers rely on the static information stored in magnetic stripe cards to steal card credentials. This data can then be copied and uploaded to a counterfeit magstripe card. If you don’t swipe, they can’t copy or clone this data.
Shimmers, on the other hand, capture data located inside the EMV microchip that is embedded into your card. The data collected will then be offloaded wirelessly via a small radio module built into the device.
How do card shimmers work?
Shimmers are very tiny, thin devices that can be fitted into a card terminal, and can read EMV microchip data much in the same way that skimmers can read magstripe data.
Fraudsters can't yet fully "clone" an EMV chip that's encoded with a valid user's information. However, they can copy the information stored on an EMV chip using a shimmer, then encode that onto a magnetic stripe card. The fraudster can use the dummy card at any card-present retailer which allows customers to use a magnetic stripe card.
Is card skimming still a thing?
Yes, card skimming is still a concern. Their use has been declining since EMV mandates went live in the US, but in 2022, researchers observed a sudden spike in skimmer-related scams. Attacks were up nearly 700% in just the first half of 2022. It is likely that card “shimmers,” or EMV skimmers, were involved in most of these reported scams.
How can you tell if an ATM has a skimmer?
Skimmers are generally loaded onto the front of a card terminal, where a card would be swiped or dipped. There will generally be some ill-fitting colors or some other sign that the device has been tampered with. Watch for these warning signs to spot a skimming device.















