What Cardholders & Merchants Should Know to Prevent Credential Stuffing Attacks
Credential stuffing attacks are a leading cause of data breaches today, mainly because 64% of people tend to use the same password for multiple, if not all, of their accounts.
The chance for hackers to succeed with credential stuffing is on the rise as more and more stolen credentials become available through data breaches. Right now, there are literally billions of these compromised login details floating around on the dark web.
However, it's entirely possible to stop credential stuffing attacks by putting the right cybersecurity strategies in place. Executives should be aware of what credential stuffing entails and what steps can be taken to lower the chances of their organizations falling prey to these attacks.
Recommended reading
- Fake Google Reviews: How to Identify, Remove & Prevent
- The Top 10 Prepaid Card Scams to Watch Out For in 2025
- How do Banks Conduct Credit Card Fraud Investigations?
- What is Smishing? How to Identify & Prevent SMS Text Scams
- How Clean Fraud Works: Tactics, Red Flags & How to Prevent
- How Card Cracking Works: Tactics, Red Flags & Prevention
What is Credential Stuffing?
- Credential Stuffing
Credential stuffing is a brute force fraud tactic that involves using bots to automatically attempt to enter stolen username and password pairs into a web form. The term “credential stuffing” refers to the fact that bots can attempt hundreds of sets of login credentials per minute until they find a match.
[noun]/krə • dent • SHəl • stəf • iNG/Credential stuffing is a type of cyberattack. Hackers use stolen usernames and passwords from one source to gain unauthorized access to accounts at another site. These stolen credentials are often obtained from past data breaches or bought from hidden markets on the internet.
To illustrate, picture a thief with a massive ring of keys, who is trying to get through a locked door. The thief tries each key to see which one opens the door. Credential stuffing is basically the digital version of this.
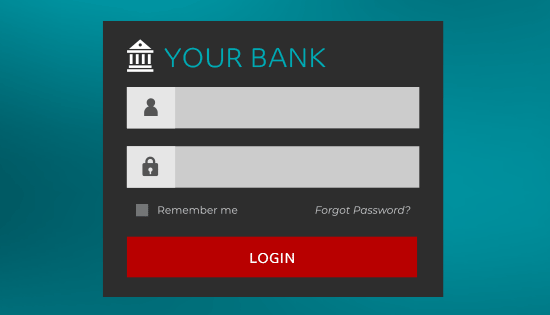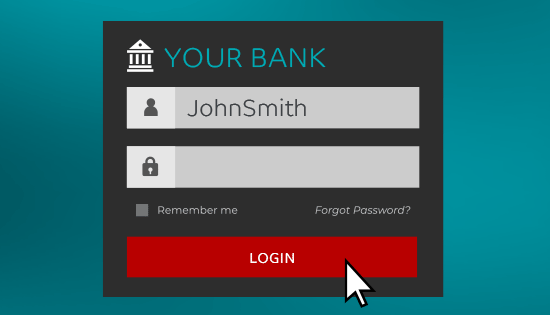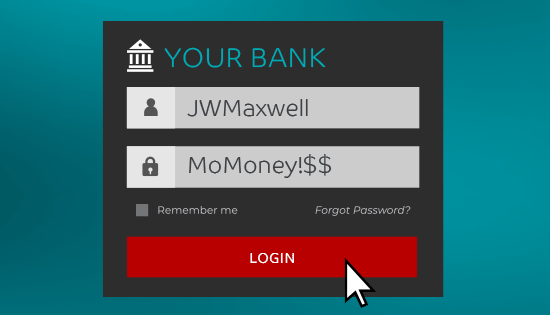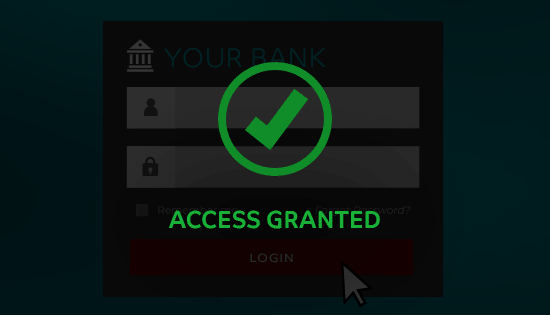
How Does Credential Stuffing Work?
In this process, the hacker uses automated programs to rapidly test these stolen login details across numerous websites. This method works because many people reuse their passwords across multiple sites. If the hacker finds a match, they can enter accounts, steal sensitive information, or cause other harm.
So, how exactly do they do it? Well, here’s how credential stuffing happens, step by step:
Step #1 | Gathering Stolen Information
The first step for a hacker is to collect lots of usernames and passwords, usually from past security breaches. These stolen details can be bought in bulk on the dark web, in various chat forums or by other means.
Step #2 | Preparing the Attack
Once they have these credentials, hackers organize them, often selecting the most likely to succeed for their attempts. This can be done manually, or credentials can be sorted using an automated process.
Step #3 | Automating Login Attempts
Hackers then use specialized software to automatically enter the stolen usernames and passwords on a wide range of websites. This software can test thousands of logins across multiple sites in a matter of seconds.
Step #4 | Gaining Unauthorized Access
If (or inevitably when) the bot finds a login that works, the hacker can then get into that account. They might look for personal information, make unauthorized purchases, or use the account in other harmful ways.
Is Credential Stuffing Effective?
When you look at the numbers, credential stuffing might not seem like a very effective tactic. This is because a lot of the credentials attempted might be out of date or mismatched for the account in question. All totaled, only about 0.1% of credential pairs will work; that’s just one in every 1,000 login attempts.
Here's the catch, though: bots can carry out these attacks super fast. One script can try millions of different username and password combos on multiple sites with little effort. Even with a 0.1% success rate, that’s still thousands of compromised accounts per attack.
So, even if it doesn't always work, credential stuffing is still a big problem because of how easy and cheap it is for hackers to keep trying until they get lucky. Plus, many people use the same password for multiple accounts. If a hacker can compromise one account, they have a solid lead on how to compromise additional accounts held by that user.
What Can Scammers Do With Compromised Accounts?
After breaking into an account, hackers might use it immediately for malicious purposes, or file away the information and save it to conduct fraud later. They can also sell the access they've gained to others in dark web markets.
Common examples include:
That's why it's really important for businesses to require both customers and employees to use strong, unique passwords for every account. They should also deploy extra security steps, like two-factor authentication, whenever possible. It makes it a lot harder for hackers to get in and protects everyone's information better.
Real-Word Examples of Credential Stuffing
Credential stuffing attacks have become so routine that there's actually a going rate for hacked accounts; a kind of twisted online marketplace, based around supply and demand.
The price tag on these stolen accounts depends on how much they're worth. So, credentials for financial accounts (banks, PayPal, Western Union, etc.) might sell for anywhere from $30 to $120. Plus, hackers are coming up with new ways to break into systems every day, and it seems like each attacker is more clever than the last.
Here are a few recent, real-world stories that illustrate just how big a problem this can be:
New York Attorney General
The office of the New York Attorney General uncovered one million exposed accounts in a 2022 credential stuffing probe, involving credentials for customer accounts at 17 well-known companies. Targeted sectors included online retailers, restaurant chains, and food delivery services.
Canada Revenue
& GCKey
According to CBC Canada, the Canada Revenue Agency found out that, out of about 12 million GCKey accounts, 9,041 were hacked using credential stuffing. They had to shut down their online services for a bit to deal with it.
PayPal
A recent PayPal breach impacted 35,000 accounts. The company has thus far not identified any unauthorized transactions. However, it was reported that the attack may have been carried out to use those thousands of compromised accounts in other schemes.
US Banks
ZDNet shared info from an FBI warning that said hackers used stolen login info to make fake check withdrawals and electronic transfers from a US bank between January and August 2020. They managed to steal more than $3.5 million in this attack.


These are some high-profile cases, but small-scale attacks happen every day. Retail accounts are hot items, for instance. Someone might pay around $30 for access to a compromised Amazon account.
Social media accounts are in demand, too. They can be used for all sorts of shady activity, from fake promotion campaigns (called “astroturfing”) to tricking someone's contacts into downloading harmful software. Prices vary by platform: a Facebook account might go for $65, Instagram for $45, and Gmail for a solid $80.
“Red Flags” of Credential Stuffing
There are some clear warning signs for which everyone should be on the lookout here. Catching these hints early can really save a lot of trouble for businesses and their customers.
- Weird Login Attempts: Getting messages about someone trying to log in or reset passwords, despite not having actually done this.
- Repeated Account Locks: If an account keeps getting locked because of too many login attempts, it may be someone repeatedly testing multiple passwords.
- Strange Account Activity: Orders or credential changes that no authorized user made.
- Failed Logins: Getting a bunch of notices about login attempts from places or devices you don't recognize.
- New Device or Location Warnings: Alerts about new devices in unusual locations accessing the account.
- Unexpected Emails or Messages: Receiving emails or messages regarding activity that no authorized user recognizes.
- Lots of Logins Attempts from One Place: Seeing many login tries, using different credentials, all from just one IP address.
- Customers Complaints: Customers reporting weird account activity or lock outs might mean a widespread attack on many accounts.
Spotting these signs early can help prevent bad actors from doing serious damage.
Businesses can use tools to watch for odd login patterns or set up challenges like CAPTCHAs to stop automated hacking attempts. Users can also make it tougher for hackers by using different passwords for different sites and turning on extra security steps, like getting a code on your phone whenever possible.
How to Prevent Credential Stuffing
No one wants to feel at risk online, regardless whether you’re a cardholder looking to keep your personal information safe or a business trying to prevent cyberattacks. This is why merchants and their customers should work together to address the vulnerabilities that lead to credential stuffing.
Here's how both card users and businesses can beef up their defenses and make it tougher for these cyber intruders:
Credential Stuffing Prevention Tips For Card Users
Credential Stuffing Prevention Tips For Businesses
Remember: even when fraud attacks do occur, consumers have some protection in the form of credit card chargebacks. This means the bank can reverse suspect transactions and re-credit the customer's account.
That’s good news for cardholders… but not so much for merchants, who end up bearing the financial burden.
Thankfully, help is available. Chargebacks911® offers a comprehensive solution to help you protect your business and keep your chargeback ratio low. Don't let chargebacks undermine your success. Take action today to secure your operations and reputation.
FAQs
What is the difference between credential stuffing and password spraying?
Credential stuffing attacks use stolen account credentials (usernames and passwords) obtained from previous data breaches to attempt to log into other websites or services.
Password spraying, on the other hand, takes a different approach. Instead of using a list of known password combinations, attackers select a common password (such as "Password123" or "Spring2020") and attempt to log in to many different accounts with it. This method relies on the statistical likelihood that at least some users will have chosen weak or commonly used passwords.
What is the best solution to credential stuffing?
To prevent credential stuffing, implement multi-factor authentication (MFA) for all user accounts. This will add a critical second layer of security. Also, educate users on the importance of using unique passwords for each account to reduce the risk of successful attacks.
What is an example of credential stuffing?
Let’s say a hacker obtains a list of usernames and passwords from a data breach at one company, then uses automated software to try those credentials on a banking website, successfully accessing several user accounts. This unauthorized access allows the hacker to transfer funds and gather personal information from the compromised accounts.
How does credential stuffing impact a user?
Credential stuffing can lead to unauthorized access to users' accounts across multiple platforms, resulting in identity theft, financial loss, and personal data compromise. The user may also face the cumbersome process of securing compromised accounts and recovering stolen assets.
What is the difference between brute force and credential stuffing?
Credential stuffing is actually a specific type of brute force attack.
Brute force attacks attempt to gain access by systematically trying every possible password combination until the correct one is found, without relying on previously stolen data. Credential stuffing, specifically, involves using previously stolen username and password combinations to gain unauthorized access to user accounts across various services, exploiting the common practice of password reuse.














