10 Ways for Merchants and Consumers to Prevent Man-in-the-Middle Attacks
A man-in-the-middle (MitM) attack is a sneaky move by which a hacker secretly intervenes and relays a conversation between two entities. The targets think they're talking directly to each other. What's really happening is the hacker has cut in the middle, passing messages back and forth, and maybe even changing them to manipulate both parties.
How do these MitM attacks work, though? How could they affect you, and how will you know when you’re most at risk? Let’s find out.
Recommended reading
- Fake Google Reviews: How to Identify, Remove & Prevent
- The Top 10 Prepaid Card Scams to Watch Out For in 2025
- How do Banks Conduct Credit Card Fraud Investigations?
- Credit Card Cloning: How it Works & How You Can Prevent It
- How Overpayment Scams Work: Signals, Examples & Prevention
- What is Third-Party Fraud? Tactics, Red Flags & Prevention
What is a Man-in-the-Middle Attack?
- Man-in-the-Middle Attack
A Man-in-the-middle (MitM) attack is a type of cyberattack by which a hacker or scammer secretly intercepts and possibly changes the messages being sent between two parties without them knowing.
[noun]/man • ən • thə • mid • əl • a • tak/
MitM attack can happen via any type of network communication. But, online attacks are, by far, the most common. During one of these attacks, the scammer sneaks into the communication path between the person sending the message and the person receiving it. Basically, they act as a hidden middleman.
The attacker might have a lot of different objectives with a man-in-the-middle attack. They just want to listen in on conversations. Or, they may intercept and change the information being communicated, with the goal of altering the meaning of what was sent.
In the same way, an attacker might steer or tweak the sharing of sensitive details such as credit card numbers or passwords. This would result in theft of funds or identity theft.
How Do Man-in-the-Middle Attacks Work?
First off, the person doing the attacking needs to avoid being noticed by the person sending the message and the person receiving it. These attacks usually succeed by taking advantage of weak spots in how the network is protected, or mistakes in how network devices are set up. They can also target unsecure communications, like those sent over public WiFi.
To pull off a MitM attack, there are two main steps the attacker needs to go through. First, they need to catch the messages being sent (intercept). Second, they might need to unlock (decrypt) those messages if they're protected.
The first step for an attacker is to grab the data you're sending out before it gets to where it's supposed to go. A common way they do this is by setting up free WiFi hotspots that don't require a password.
They give these hotspots names that sound like they belong to a nearby business and trick people into connecting. The scammer may post up in front of Starbucks, and set up a WiFi hotspot called “Starbucks Free WiFi,” for example. Once someone connects, the attacker can see everything they're doing online.
For attackers who want to be a bit more hands-on, they might try these tricks:
- IP Spoofing: This is when an attacker pretends to be a certain website or service by changing information in the data packets sent over the Internet. So, when you try to visit a website, you end up on the attacker’s fake site instead.
- ARP Spoofing: Here, the attacker tricks a network into thinking their computer is another computer on the network. This means any data meant for the real computer gets sent to the attacker instead.
- DNS Spoofing: This involves messing with a website's address record on the DNS server (which helps your browser find websites). So, when you try to visit a website, you get redirected to a fake one controlled by the attacker.
Some data will be protected, as with SSL, which makes data unreadable to snoops. So, the attacker has to crack it open without anyone noticing. They have a few sneaky ways to do this:
- HTTPS Spoofing: The attacker tricks your browser with a fake security certificate when you try to visit a secure site. This lets them see the data you're entering on that site.
- SSL BEAST: This method takes advantage of a weakness in older security protocols to sneak a look at secure information, like the cookies that keep you logged into websites.
- SSL Hijacking: When you try to connect to a website, the attacker jumps in and pretends to be both you and the website, seeing everything you send and receive.
- SSL Stripping: The attacker makes your browser think it's using a secure connection when it's not. They see everything in plain text while you think you're safely encrypted.
These methods show how crafty attackers can be in intercepting and messing with your data. But, how big a problem is this, actually?
The Impact of Man-in-the-Middle Attacks
MitM attacks are widespread. But, that’s mainly because they're pretty easy to pull off.
The IBM X-Force Threat Intelligence Index reports that 35% of hacking activities include MitM attacks. MitM tactics are especially harmful because attackers can sneak into networks without being noticed, steal personal information, and leave without a trace. It could be months before anyone even notices the breach happened.
Devices usually try to connect to the strongest WiFi signal available by default. So, if someone isn't careful, their device might link up with a fake WiFi network without noticing. Even if these attacks are eventually caught and stopped, the hackers might have already made off with valuable data.
Businesses hit by major cyber attacks, including MitM attacks, face a high risk of failing. In fact, they have a 60% chance of going bankrupt within just 6 months.
A big reason why MitM attacks are so common is that WiFi technology itself has weaknesses. For example, if your device has ever connected to a WiFi network named "Coffee Shop," it will automatically try to connect to any network with that name in the future. This flaw makes it easy for hackers to set up fake WiFi networks, trick devices into connecting, and steal login credentials. That's why MitM attacks are such a frequent problem.
5 Real-World Examples of MitM Attacks
MitM attackers don't care if it's a big company they're messing with, or just regular folks. Any target is a legitimate target. That said, I have a few high-profile examples of these attacks that I wanted to spotlight:
#1 Belgacom Hack
In 2013, a phone company in Belgium called Belgacom (now known as Proximus) was hit by a sneaky MitM attack. It turns out spies from Britain were behind it. They tricked company workers into visiting bad websites that put spy software on their computers. This let the spies listen in on private phone calls and internet activity.
#2 Superfish Adware
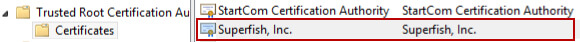
Lenovo laptops had adware called Superfish installed before they were sold. It would mess with your internet searches and websites to show you extra ads. The scary part? It could also sneak a peek at secure web pages, like when banking or shopping forms, which should have been private.
#3 Equifax Mobile
Equifax was the target of a now-infamous attack in 2017. Almost 150 million Americans had their personal info leaked. It turns out that Equifax wasn’t always using secure connections for its mobile apps. This made it easy for hackers to grab people's data when they checked their accounts on their phones.
#4 DEFCON WiFi Attack
DEFCON is an annual convention for hackers. In 2018, folks set up a fake WiFi network during the show to demonstrate how simple it is to pull off a MitM attack. Even a well-known politician got caught up in the trick, proving that pretty much anyone could get their data stolen if they're not careful about which WiFi they connect to.
#5 Twitter API Misconfiguration
In July 2020, a weakness in the setup of X (formerly Twitter) let hackers mess with how the site communicates with other services online. They could sneak in between Twitter and these services, stealing sensitive info like login details from several large accounts. So, even big social media sites are vulnerable to these attacks.
How to Detect a Man-in-the-Middle Attack
Detecting a man-in-the-middle attack starts with being alert to certain clues that something fishy might be happening. Here are a few things to watch out for:
Beyond these red flags, I also suggest that you use network security tools. There are tools and software available that can help detect MitM attacks by monitoring your network for any suspicious activity. These tools can alert you if they find something out of the ordinary.
10 Tips to Prevent Man-in-the-Middle Attacks
Both merchants and consumers can adopt more detailed and robust security practices to boost their defenses against MitM attacks. Here are 10 tips to get you started:
#1 | Use HTTPS
Secure your website with HTTPS, which encrypts the data exchanged between a user's browser and the website, making it difficult for attackers to intercept and read the data. For consumers, it's crucial to check for the “HTTPS” prefix and the lock icon in the browser address bar before entering any personal information.
#2 | Deploy VPNs
A Virtual Private Network (VPN) creates a secure tunnel for internet traffic, encrypting data from end to end. This is especially important for merchants handling sensitive customer data and for consumers using public or unsecured WiFi networks. It prevents attackers from easily accessing transmitted data.
#3 | Secure WiFi Networks
For merchants, securing WiFi networks means using strong encryption like WPA2 or WPA3. It also means changing default passwords and regularly updating them. Consumers should avoid public WiFi for transactions; if necessary, using a trusted VPN can add a layer of security.
#4 | Keep Software Updated
Software vulnerabilities are frequently exploited by attackers to perform MitM attacks. Ensuring all systems and applications are up-to-date with the latest security patches can close these vulnerabilities and protect against exploitation.
#5 | Enable Two-Factor Authentication (2FA)
Add a second layer of security beyond just a password. For instance, requiring a text message code or an authentication app, as this can significantly hinder attackers. This will help even if they manage to intercept your password.
#6 | Learn About Phishing Scams
Awareness and education about the risks of phishing emails, which often serve as the entry point for MitM attacks, are crucial. Both merchants and consumers should be cautious of emails that ask for sensitive information, or that urge immediate action.
#7 | Monitor for Suspicious Activity
Regular monitoring of accounts and networks for any signs of unauthorized access or unusual activity can help in the early detection of MitM attacks. Implementing alert systems for unusual transaction patterns or login attempts can provide immediate warnings of potential breaches.
#8 | Use Trusted Security Tools
Using reputable security solutions such as firewalls, antivirus software, and intrusion detection systems can provide a solid defense against various cyber threats, including MitM attacks. These tools can detect and block malicious activities and traffic patterns associated with these attacks.
#9 | Verify Digital Certificates
Digital certificates authenticate a website's identity and ensure secure connections. Merchants should keep their website's certificates up to date, and consumers should heed browser warnings about sites with invalid certificates, as this may indicate a MitM attack attempt.
#10 | Implement DNS Security Measures
DNS spoofing can redirect users to fraudulent sites. DNSSEC (Domain Name System Security Extensions) provides a layer of security that verifies the authenticity of the domain name's response, preventing redirection to malicious sites set up by attackers.
Stay Informed. Stay Safe.
Remember: a lot of cyberattacks happen because of simple mistakes people make without realizing it.
Businesses should teach their employees about the risks of man-in-the-middle attacks and make sure everyone goes through training on how to stay safe online. This can limit their exposure to risk, safeguard sensitive information, and maintain the integrity of online transactions and communications.
For consumers, staying up-to-date on the latest tactics and schemes used by fraudsters is crucial. This could make the difference between staying safe online and becoming a victim.
FAQs
What is a man-in-the-middle attack?
A man-in-the-middle (MitM) attack is a type of cyberattack where a hacker or scammer secretly intercepts and possibly changes the messages being sent between two parties without them knowing. This kind of attack happens during digital conversations, like those over the internet or through other types of network communications. In a MitM attack, the attacker sneaks into the communication path between the person sending the message and the person receiving it, acting as a hidden intermediary or “middleman.”
What is a real life example of a man-in-the-middle attack?
Equifax, a big company that knows a lot about people's money, got hacked big time in 2017. Almost 150 million Americans had their personal info leaked. It turns out that Equifax wasn’t always using secure connections for its mobile apps, making it way too easy for hackers to grab people's data when they checked their accounts on their phones.
How is a man-in-the-middle attack executed?
In a MitM attack, a hacker secretly intercepts and may alter the communication between two parties who believe they are directly communicating with each other by positioning themselves in the digital conversation path. The attacker can then listen in, manipulate the exchange of information, or impersonate either party to gain access to sensitive data.
How bad is a man-in-the-middle attack?
MitM attacks are extremely harmful because they allow attackers to steal or manipulate sensitive information without detection, potentially leading to identity theft, financial loss, and a significant breach of privacy. This type of attack undermines trust in digital communications and can have devastating consequences for individuals and organizations alike.
What are the dangers of a man-in-the-middle attack?
MitM attacks pose a specific danger by enabling attackers to intercept, alter, or steal sensitive data exchanged between two parties, leading to potential financial fraud, data breaches, and compromised personal or corporate security. This undermines the integrity of communication systems and exposes individuals and organizations to significant risks.
















