How Merchants Can Use Proxy Piercing to Help Prevent Fraud
At the risk of stating the obvious, eCommerce merchants seldom actually see their customers. For the most part, that’s fine. But there are fraudsters out there who have learned how to take advantage of this anonymity.
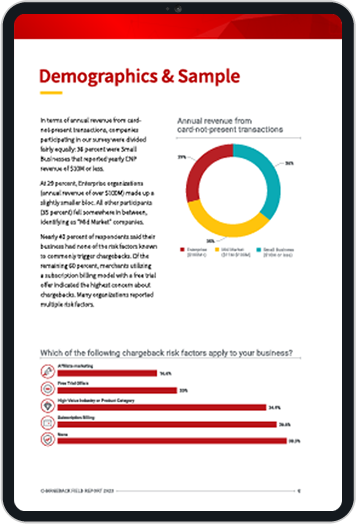
When you’re taking online orders, there aren’t many ways to know for certain that the buyer is the actual authorized cardholder. In fact, you may not even know if the “buyer” is a human being at all.
You can’t fight back if you don’t know who your enemy is. Fraudsters leverage that fact by hiding their identity from you. One way they do this is by using proxy servers, which make it seem like their activities are coming from someone else.
Fortunately, there are technologies you can use to fight back. One such tool is proxy piercing. In this post, we’ll talk about proxies, plus look at the role a proxy piercing solution may have in your overall fraud management strategy.
Recommended reading
- What is Mastercard SecureCode? Here’s How it Works
- Reverse Email Lookup: Tips, Tools & How to Detect Fraud
- ECI Indicators: How to Understand 3DS Response Codes
- How Device Fingerprinting Works: Use Cases, Trends & More
- CVV2: How it Works | Rules & What Comes Next
- How to Detect Fraud: Top 20 Tips to Stop eCommerce Scams
What Is Proxy Piercing?
- Proxy Piercing
Proxy piercing is a technology that enables hosts to determine whether a customer is attempting to mask their IP address by using a proxy server.
[noun]/prôk • sē • pir • sing/
It’s a fancy term. But, proxy piercing basically just means you’re checking to see if a buyer is using a third-party server to mask their identity. This is done through a small test that typically happens in the background, unnoticed by the user.
There are valid reasons for using a proxy, such as protecting one’s data security. That said, the very things that make proxies legitimately useful also make them an excellent tool for abuse. Proxy fraud is a way for criminals to mask their identity to get away with scams. Proxy piercing tools are designed to prevent that.
The most basic detection programs can tell you that a proxy is being used, but won’t reveal the user’s actual IP address. More sophisticated programs may be able to “pierce” the veil of the proxy server, providing the user’s original IP address and even their physical location.
How Do Criminals Use Proxy Servers?
Fraudsters love using proxy servers because it keeps you from knowing who they are. Your having that information won’t stop them, but it can make their job more difficult.
There are different types of proxies, but we’ll be focusing on two in particular: data center proxies (which use the IP address of the host server) and residential proxies, which use actual residential IP addresses to make them look more like real consumers. Of the two, fraudsters typically favor residential proxies, because an IP address originating from a home connection is less likely to raise suspicions.
By using a proxy server, fraudsters can bypass tools designed to detect repeated failed login attempts. This also allows for quick switching between multiple proxies, fooling some velocity restrictions and making repetitive orders seem to come from different IP addresses. Fraudsters may take advantage of this feature to carry out other activities, too, like commit affiliate fraud.
Cyber criminals may even spoof their IP geolocation information. They can hide the fact that an order came from a country or region considered to be at “high risk” for fraud.
How Does Proxy Piercing Work?
Proxy piercing works by deploying a small bit of code on the user’s device to determine if the real IP address matches the one being used in the transaction.
The goal of proxy piercing is to flush out fraudsters who use some kind of intermediary to hide their identity. It works by deploying a small bit of code on the user’s device that snags the IP address from the buyer’s order.
Using public information, in-house data, and other sources, the customer’s IP address is compared against addresses, proxies, and Virtual Private Networks (VPN) known to be used by fraudsters. If a proxy is detected, the program can deny the order and even ban the server’s IP address. The process goes something like this:
Depending on how your parameters are set, proxy piercing can be vulnerable to false positives. You could end up rejecting legitimate buyers by relying on the originating IP address alone.
You should review results alongside additional indicators, such as the customer’s purchasing history, or whether the order used a data center proxy or a residential proxy. These may all play a role in deciding if the user is, in fact, a bad actor.

Proxy Piercing Techniques
A variety of different tools and techniques can be used to uncover the true IP addresses of users, enabling you to identify suspicious orders. For example:
Session Monitoring
Session monitoring combines device fingerprinting with the tracking of user interactions such as page views. Monitoring can be spoofed if a fraudster is looking for it. On the plus side, this technique is better at preserving user privacy.
WebRTC
WebRTC enables browsers to have real time audio-visual (AV) communication without an additional program or app. WebRTC leaks can be used as a way of detecting proxies, but you might want to weigh it against user privacy concerns.
HTTP Headers
In some cases, HTTP headers can be automatically examined for information about the client's IP address. This is a bit of a long-shot, though; for it to work, this technique requires a broken VPN service or an incorrect proxy configuration.
DNS Leaks
Along the same lines, DNS leaks may uncover a user's true IP address if the proxy or VPN is properly configured, but the fraudster makes a mistake setting things up on their end. This is a hit-or-miss proposition, at best.
Some proxy piercing methods were effective at one time but are now considered obsolete. Tools like Adobe Flash, Java Applets, and ActiveX Controls are ineffective because they’re no longer being supported by the major browsers.
How Effective Is Proxy Piercing?
Proxy piercing uncover the use of proxy servers, but the technology is unreliable, easily circumvented, and the results are of limited actual use.
Proxy piercing has been proven to work. Unfortunately, it’s comparatively simple for a skilled fraudster to get around. As time goes on, new technologies are making it easier for fraudsters to circumvent proxy fraud checks.
Plus, the actual benefit of knowing an IP address is limited, for one really big reason: most IP addresses are temporary.
Status IP addresses are like a phone number; they can only be assigned to one device at a time. Most residential IPs are dynamic, though. This means they can change over time (sometimes every few hours).A blacklist can be outdated almost as quickly as it’s created. An IP address you add to your blacklist may or may not be tied to a completely different PC tomorrow. You could end up blocking a legitimate user while a scammer slips by to attack you a second time.
Valid Reasons for Using a Proxy Server
Proxy servers may be legitimately leveraged for security purpose, meaning their presence may not necessarily indicate fraud.
Proxy piercing isn’t a completely outdated prevention tool. But, knowing that a customer is using a proxy doesn’t necessarily mean they’re committing fraud. In fact, there are situations where using a proxy server is the best choice.
Some consumers use proxies to keep from sharing location and behavior data with browsers, search engines, and websites. Social media sites, in particular, are notorious for gathering user data for marketing and other purposes. A proxy server can help users maintain anonymity.
Public shared networks found at airports, coffee shops, or other locations can make users vulnerable to outsider tracking of data spying. The use of VPNs can help safeguard against these threats. In more extreme scenarios, users in “closed” countries might employ a proxy server to evade government censorship or access restricted websites in their countries.
These could be real customers, despite the use of a proxy. But, if you rely too much on proxy piercing as an indicator, you could end up blocking good buyers.
Is Proxy Piercing Worth It?
Proxy piercing may work, but should only be used as one indicator among several involved in the decision whether to accept or reject a transaction.
While using a proxy is not a guaranteed sign of fraud, it can be a helpful indicator. Once you have the true IP address, it can be compared against lists of known good and bad IP addresses.
But, as we’ve seen, those lists may not be reliable. And, even the best proxy-piercing services or software can’t catch every instance of fraud. Depending solely on proxy detection to prevent fraud is risky.
Plus, no type of fraud prevention will help against post-transaction threat sources. Friendly fraud — illegitimate disputes coming from actual cardholders — can happen months after the sale. At that point, knowing which IP address the order came from is meaningless.
Effective protection from the long-term impact of fraud and chargebacks requires a comprehensive approach that addresses every aspect of the problem. Unfortunately, implementing and maintaining such a strategy can take up a lot of time and resources.
The experts at Chargebacks911® have been involved with all areas of chargeback prevention and revenue recovery for over a decade. We can save you time and headaches and up your ROI. For more information, contact us today.
FAQs
How does proxy piercing work?
Proxy piercing works by analyzing network traffic and identifying patterns that may indicate where a proxy server is being used. This can include unusual IP address changes, inconsistencies in the data packets, or discrepancies in the headers. While these do not necessarily mean the user is a fraudster, it does raise suspicions.
Is using a proxy server illegal?
No. As long as proxies are used for legitimate purposes, they are in most cases legal. There may, however, be certain situations where their use is questionable, either legally or ethically. If in doubt, consult with a legal professional.
What is proxy phishing?
The criminal may pose as an IT professional or falsely claim that it different settings would increase performance. It is then possible for the fraudster to secretly install malware that re-directs webmail and other online traffic through bogus proxy servers. The criminal controls the proxies, and are able to steal usernames and passwords when forms are submitted.
Why would someone use a proxy?
Proxy servers offer protection between the user and the internet, maintaining the anonymity of website traffic. They can play a vital role in protecting reporters, whistleblowers, and other parties where anonymity is a primary concern. Proxies helps provide data security, can improve speeds, and control internet usage.